Vulnerability Info
Publicly Published
Jan 22, 2024
Patch Info
Patched version 7.2.2 was released in Jan18, 2024
About File Manager Plugin(As of Writing)
Active Installations
1+ million
Total Downloads
21 million
What Kind of Plugin is This?
You will be able to edit, delete, upload, download, compress, copy and paste files and folders directly from the WordPress admin screen by using the plugin. There is a backup and restore function as an accompanying function.
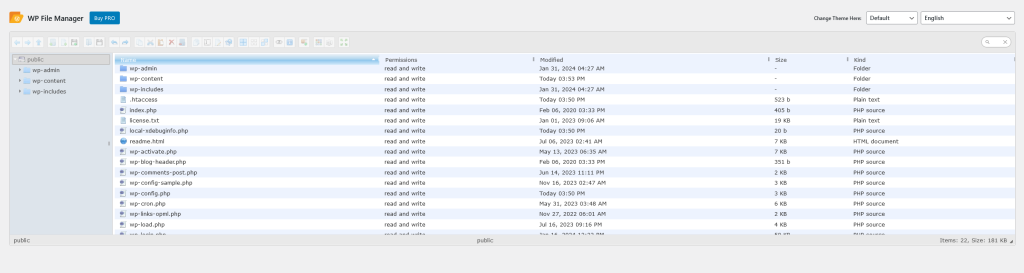
Vulnerability Details
Cause of the Vulnerability
Improper random value generation range for PHP’s rand function
A value between 0 and 9999 is randomly generated and used as part of the backup file name.
Therefore, the generated backup file name is
backup_[year]_[month]_[day]_[hour]_[minute]_[second]_[0-9999 random]-[backup file type].
With this specification, if an attacker can guess the date and time of the backup was created, there is a high possibility that the attacker will be able to retrieve the backup file.
The Code Causing the Problem
$file_number = 'backup_'.date('Y_m_d_H_i_s-').rand(0,9999);The plugin is designed to use .htaccess
Direct access to backup files and log files using URLs is restricted by creating .htaccess in the backup directory.
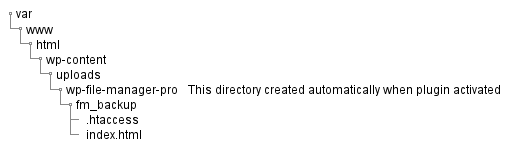
However, if you are using an environment where .htaccess cannot be used, such as the one below, you will be able to directly access backup files and log files without logging in or requiring any privileges.
- nginx server
- Apache server
If AllowOverride None is left in httpd.conf for the /var/www/html directory
Possibility of guessing the plugin activation date and time
According to the specifications, index.html is automatically generated in the backup directory when the plugin is activated.

As mentioned above, anyone can download this file if .htaccess is not working, and by obtaining the last update date and time from the file’s metadata, you can obtain the activation date and time of the plugin.
The combination of these causes makes it easy to retrieve backup files if an administrator runs a backup within minutes of activating the plugin.
Vulnerability Countermeasures for Plugin User Side
If an environment in which .htaccess can be executed or continuous access is denied in a short period of time, it would be difficult for an attacker to attack this vulnerability, and it couldn’t become a realistically exploitable vulnerability.
Additionally, since there are many other plugins that depend on the .htaccess execution environment, we believe that users can take measures against this issue by taking the following measures.
Installing security plugins
Most security plugins have the ability to block continuous suspicious access.
I think that installing the free version can be a countermeasure.

Using a web server that supports .htaccess
Since the use of .htaccess is often a prerequisite for other plugins, so we recommend using an Apache server that supports .htaccess.
Vulnerability Countermeasures for Plugin Vendor Side
If the range of random values generated by the rand function is expanded, vulnerabilities are less likely to occur, but the rand function cannot be said to be generated completely randomly due to its specifications.
Therefore, I recommended that the vendor make the following changes to the source code.
Using openssl_random_pseudo_bytes function [Recommended]
Generate unpredictable file names using the openssl_random_pseudo_bytes function, which generates cryptographically secure values.
Example
bin2hex(openssl_random_pseudo_bytes(1)) # Ex. 9f
bin2hex(openssl_random_pseudo_bytes(4)) # Ex. 305a867dmd5 function + rand function
It is safer than using only the rand function, but it is not as safe as the openssl_random_pseudo_bytes function. However, in order to maintain PHP version compatibility, I think we should consider adopting this idea.
Example
substr(md5(rand()), 24) # Ex. 28b24c84Additionally, although I have not recommended below countermeasures to vendors, I believe that the following measures are effective in making the website more secure.
Determining the execution environment
Determine whether .htaccess is available within the plugin, and if it is not available, add the following functionality.
- Recommend user to use Apache server
- Warning to add access restriction description to nginx.conf when using nginx server
- Disable features that require the use of .htaccess
Use .php as a backup file
I think that by making the backup file with .php, it will not be possible to download it without logging in or having permissions.
(Untested)
Patch
The following changes have been made in patched version 7.2.2.
Before Patched
$file_number = 'backup_'.date('Y_m_d_H_i_s-').rand(0,9999);After Patched
$file_number = 'backup_'.date('Y_m_d_H_i_s-').bin2hex(openssl_random_pseudo_bytes(4));